Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


DarkGate is a loader, which possesses extensive functionality, ranging from keylogging to crypto mining. Written in Delphi, this malware is known for the use of AutoIT scripts in its infection process. Thanks to this malicious software’s versatile architecture, it is widely used by established threat actors.
|
Loader
Type
:
|
ex-USSR
Origin
:
|
|
15 November, 2018
First seen
:
|
23 April, 2025
Last seen
:
|
|
Type
:
|
ex-USSR
Origin
:
|
|
15 November, 2018
First seen
:
|
23 April, 2025
Last seen
:
|

 1107
1107
 0
0
 2271
2271
 0
0

 2083
2083
 0
0
DarkGate is a loader malware family that was first detected in 2018 and has since been continuously undergoing serious development, significantly expanding its functionality. This malicious software is notable for the use of various evasion techniques, such as process hollowing.
It is distributed based on the malware-as-a-service (MaaS) model by its developer who goes by the name RastaFarEye on popular Darkweb forums. According to the creator of the malware, they have been developing it since 2017.
As of the beginning of 2024, RastaFarEye offers only 30 seats per month to those willing to purchase a subscription, which is priced at $15,000/mo. The malware has been observed to be used by known threat actors in different attacks involving data theft and extortion. Operators get to control the malware via a special panel.
DarkGate is a multi-functional malware, meaning that it can be employed for a range of malicious purposes. Here is an overview of its key capabilities:
The DarkGate virus achieves persistence, making sure it stays on the computer even after a restart, in several ways. For instance, it can create a shortcut in the Startup folder or change a setting in the registry. Additionally, it employs Asynchronous Process Call injection.
In order to evade antivirus software, DarkGate has the functionality to check the presence of a list of popular security products on the system. It also has an anti-sandboxing capability, where it can detect a virtual machine environment and halt or adjust its execution.
All the communication with the command and control (C2) server is performed via HTTP and is obfuscated.
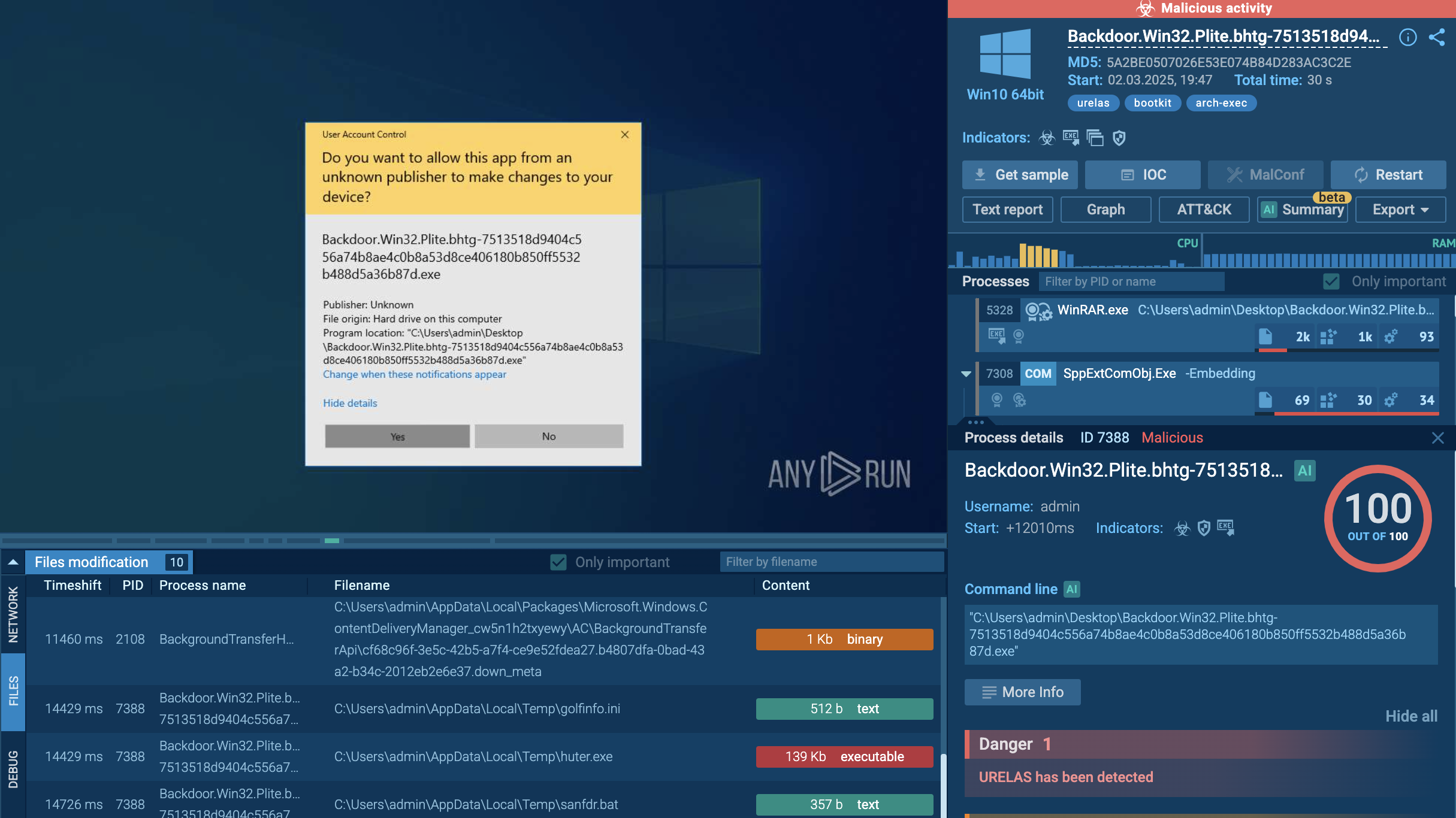
Despite having an anti-sandboxing capability, DarkGate can be easily analyzed in ANY.RUN. As a result, we can easily detect the malware and observe its activity by simply uploading its sample to the sandbox.
 DarkGate`s threat details demonstrated in ANY.RUN
DarkGate`s threat details demonstrated in ANY.RUN
The execution chain of DarkGate may vary depending on the versions and other factors. In some instances, the entire execution chain is contained in a single file that facilitates all activities post-infection. Let's examine our sample.
DarkGate may perform process hollowing into certain processes within the infected operating system. This can include TabTip32, BraveUpdate, MicrosoftEdgeUpdate, ielowutil, or, in our case, GoogleUpdate. This malware often utilizes AutoIT scripts and files for injection and execution of shellcode and other malicious activities. The primary malicious activities are executed through the injected GoogleUpdate process. It adds itself to the startup directory, checks for the presence of antivirus software, connects to the command and control server (C2), downloads payloads, and more.
To collect up-to-date intelligence on Darkgate, use Threat Intelligence Lookup.
This service gives you access to a vast database filled with insights from millions of malware analysis sessions conducted in the ANY.RUN sandbox.
With over 40 customizable search parameters, including IPs, domains, file names, and process artifacts, you can efficiently gather relevant data on threats like Darkgate.
 Search results for Darkgate in Threat Intelligence Lookup
Search results for Darkgate in Threat Intelligence Lookup
For example, you can search directly for the threat name or use related indicators like hash values or network connections. Submitting a query such as threatName:"darkgate" AND domainName:"" will generate a list of files, events, domain names, and other data extracted from DarkGate samples along with sandbox sessions that you can explore in detail to gain comprehensive insights into this malware’s behavior.
Like other common malware families, including Remcos and njRAT, DarkGate infiltrates systems through deceptive emails.
However, instead of directly embedding malware into an email attachment, DarkGate typically utilizes malicious links that direct users to compromised websites hosting MSI installer files. When unsuspecting users download and execute these infected MSIs, the DarkGate malware silently installs itself on their computers. Once embedded, DarkGate begins to steal sensitive information and perform other similar actions.
DarkGate is an extremely capable malware that is operated by infamous threat groups, which puts it on a list of major cybersecurity concerns. To ensure your organization has the capacity to avoid becoming another victim of the malware, you need to have access to up-to-date information on DarkGate.
Utilize the ANY.RUN sandbox to examine the latest samples of DarkGate and gather up-to-date insights into their behavior patterns. Uncover the TTPs employed by the malware and collect its indicators of compromise. Leverage ANY.RUN's interactive malware analysis approach to safely interact with the malware as if on your own device, extracting even more relevant information.
Try ANY.RUN for free – request a demo!